Most people don’t like others snooping around in their personal information. That includes their healthcare information. Because of the Health Insurance Portability and Accountability Act (HIPAA), people in the business of healthcare especially don’t want anybody intruding on their patient data.
Most people don’t like others snooping around in their personal information. That includes their healthcare information. Because of the Health Insurance Portability and Accountability Act (HIPAA), people in the business of healthcare especially don’t want anybody intruding on their patient data.
Businesses must comply with the HIPAA rules governing handling and protecting the privacy of healthcare Patient Health Information, whether in physical (PHI) or digital (ePHI) format. The penalties for violating HIPAA laws can be quite severe. This applies to actions by your company, its employees and partners, as well the inappropriate use and disposal of equipment used to process patient information, such as printers, faxes, and scanners.
HIPAA and PHI/ePHI
Most people have heard of HIPAA. Whenever you go to your doctor, you need to provide your patient and insurance information for further care. This requires informing you of your privacy rights and how the practice will use this information, such as storing it in an Electronic Health Records system so it will be protected and available to the practitioners delivering health services.
The origin of HIPAA lies in the 1996 law that allows workers to carry forward their insurance and healthcare rights when they change jobs. Since then, HIPAA has evolved to be a far more comprehensive law. According to Stellar Data Recovery, the Privacy Rule of HIPAA marks all individually identifiable health information as protected health information. PHI includes, but is not limited to the following:
- All demographic data
- Common identifiers like name, address, social security number, etc.
- All past, present, and future information related to the physical and mental health condition of an individual
- Healthcare provision available to an individual
- Past, present, and future payment for the healthcare provisions
Ignorance Is Risk
Every day, PHI data is at risk of being accessed by people who should not have access. Typically, these breaches are for financial gain. Ransomware attacks, where hackers hold health care facilities hostage until they are paid a ransom, and other types of security breaches have been increasing every year. The HIPAA Journal reported that in 2009, there were 18 breaches of over 500 records. This number increased to 642 in 2020 (1.76 per day), including:
- Hacking/IT incidents with malware – 429
- Unauthorized access/disclosures consisting of employee errors, negligence, acts by malicious insiders – 143
- Loss/Theft of PHI and unencrypted ePHI – 54
- Improper disposal of PHI/ePHI – 16
Even accidental incidents can expose your company to risk. For example, in 2019, an eye doctor practice discovered historic records of its patients had been discarded in a dumpster instead of being securely destroyed. This affected 7,983 patients. The records contained information such as names, addresses, dates of birth, Social Security numbers, clinical information, and billing information related to patients who visited the practice between 1997 and 2003. Fortunately, with the help of law enforcement, the practice was able to quickly respond and determine that it was unlikely that any third party had access to the information.
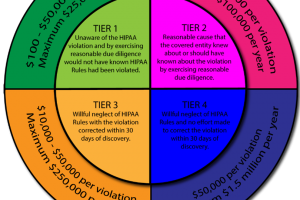
Ignorance offers no protection from HIPAA violation penalties which can be severe with multi-million-dollar fines, ranging from Tier 1 to Tier 4:
- Tier 1 – unaware of HIPAA violation ($100 – $50,000/violation)
- Tier 2 – reasonable cause company knew about violation ($1000 – $50,000/violation)
- Tier 3 – Willful neglect with correction within 30 days of discovery ($10,000 – $50,000/violation)
- Tier 4 – Willful neglect of rules and no effort to remedy within 30 days of discovery ($50,000/violation)
How can you Protect Your Business and Data?
It is crucial any organization that administers healthcare information (Think of your own HR Department) to protect PHI/ePHI data, by continually training employees, updating threat detection technology, and implementing effective protection policies and procedures.
The best practice is to implement policies and procedures that keep you in full regulatory compliance. An expert in IT Asset Disposition (ITAD) processes such as Castaway Technologies can assist you in ensuring that your business will pass an independent audit by managing and recording everything critical to proper electronics disposal including:
- Chain of Custody
- Certification of proper E-Waste disposal
- Serialized Inventory Audits
- Detailed Data Destruction Records
- Transfer of Ownership
Castaway can cost-effectively remove and document all of your retired data-bearing assets according to HIPAA regulations. You’ll be assured that disposal is safe, secure and compliant. And importantly, you’ll have accurate documentation for every IT asset handling and disposal requirement.
For further information about HIPAA compliance in matters concerning your offline electronic assets, contact us online or give us a call at (978) 208-4730.